Evidence-Driven, Ethical Solutions for PII & PHI Data Management
 Programs serving protected or vulnerable populations must ensure that sensitive personal information is handled with the highest level of care. Whether supporting youth, justice-involved individuals, families in crisis, pregnant women, or people receiving health and social services, protection of PII is a core ethical and safety issue.
Programs serving protected or vulnerable populations must ensure that sensitive personal information is handled with the highest level of care. Whether supporting youth, justice-involved individuals, families in crisis, pregnant women, or people receiving health and social services, protection of PII is a core ethical and safety issue.
Need to protect personal human services information (PII/PHI)
Programs commonly need to meet requirements related to personally identifiable information (PII) and personal health information (PHI). For some, collection of information is part of standard case referral, intake or planning processes. For others, there are more complex requirements governing interaction. These may include:
- IRB protocol compliance
- Internal or grant-driven data governance expectations
- Interagency role-based access and documentation standards
- State privacy laws
- HIPAA security expectations (even when not directly regulated)
- CJIS requirements for criminal justice information
- 42 CFR Part 2 restrictions on substance use treatment data
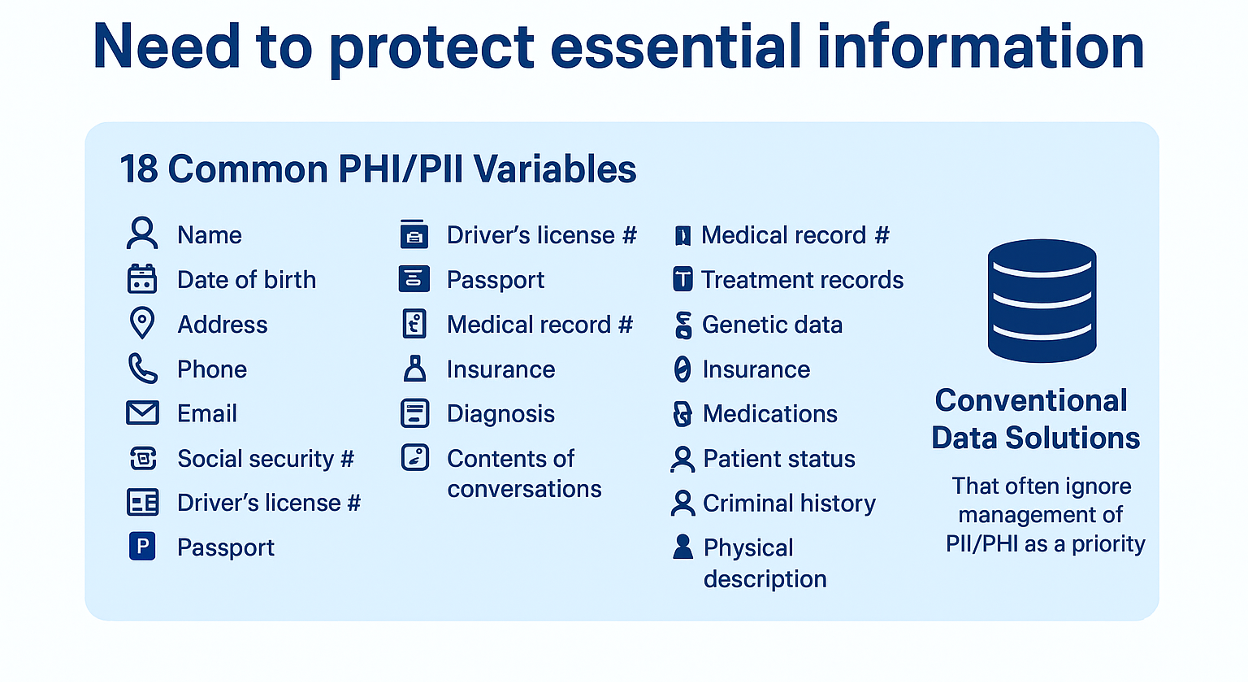 Even when not legally required, many programs adopt strict standards for management for PII/PHI among sensitive or vulnerable populations in recognition of the added risk these populations can be exposed to or with ethical considerations in mind, this information carries higher risk if mishandled. Managing a robust policy for collection and management of PII/PHI is good initial considerations. For example, one may think about what requirements does our project site or program have in place for :
Even when not legally required, many programs adopt strict standards for management for PII/PHI among sensitive or vulnerable populations in recognition of the added risk these populations can be exposed to or with ethical considerations in mind, this information carries higher risk if mishandled. Managing a robust policy for collection and management of PII/PHI is good initial considerations. For example, one may think about what requirements does our project site or program have in place for :
- Client identity verification and duplicate prevention
- Secure storage of PHI/PII
- Role-based access controls across multi-agency teams
- Consent and release-of-information (ROI) tracking
- GDPR, CJIS- and HIPAA-aligned environment controls
- Audit logs for every data access or modification
- Data minimization and field-level permissions
- Automated exports or reports
- Secure data-sharing workflows (not sharing information via email attachments)
These requirements shape how organizations operate—and failing to meet them invites risk, funding challenges, and community trust issues. In most cases, paper-based and outdated legacy tools fail to offer solutions for automated management of these policy.
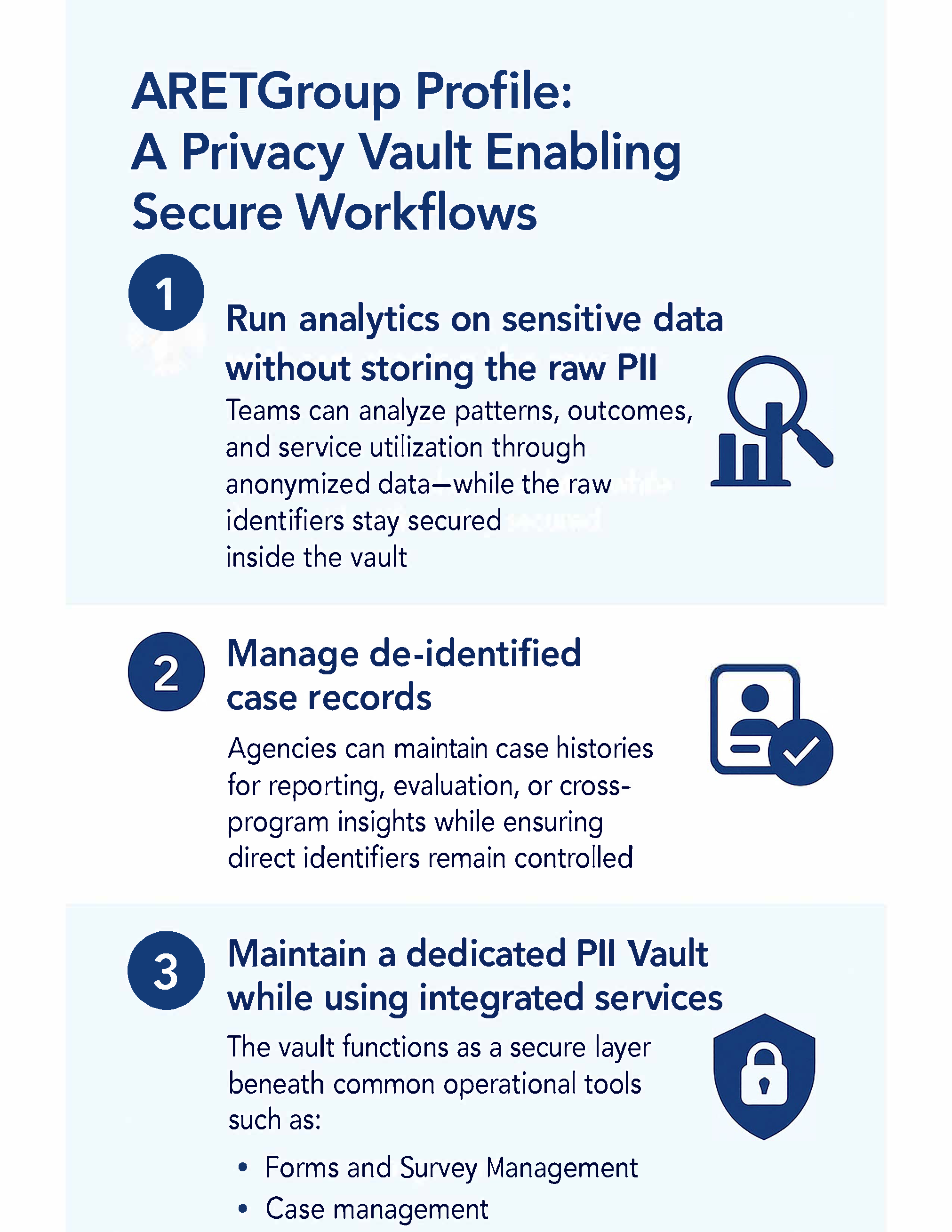
ARETGroup Profile tool is a privacy vault for sensitive human services data
Similar to the way payment systems isolate financial data for higher levels of security and compliance, ARETGroup Profile isolates PII/PHI data in a secure setting, governed by client PII/PHI policy and standards.
The Profile tool protects and manages:
- PII (Personally Identifiable Information)
- PHI (Protected Health Information)
- HIPAA-regulated data
- GDPR-covered data
- CJIS-related criminal justice data
- Any user-defined “high-risk” fields
Data stored in the vault is fully isolated from the case record and guarded by policy-based and role-based access control policies. The privacy vault enables workflows for organizations that need to achieve the following major value propositions in their regular workflow.
1. Run analytics on data without storing the raw PII. Teams can analyze patterns, outcomes, and service utilization through anonymized or tokenized data—while the raw identifiers stay secured inside the vault.
2. Manage de-identified case records. Agencies can maintain case histories for reporting, evaluation, or cross-program insights while ensuring direct identifiers remain controlled.
3. Maintain a dedicated PII Vault while using integrated services. The vault functions alongside integrated ethical human services data solutions for Case Management, Forms Management, Survey Management and Dashboard Management. As a powerful all-in-one for ethical data management.
As programs evolve and the demand for secure data practices increases, organizations that invest in strong privacy foundations will be best positioned to serve their communities effectively. And, protecting sensitive information doesn’t have to come at a high price. If you're exploring ways to strengthen your data protection strategy, now is the time to assess whether your current tools are meeting today’s requirements.

